🔒 Hands-On Cybersecurity Course + INTERNSHIP 🔒
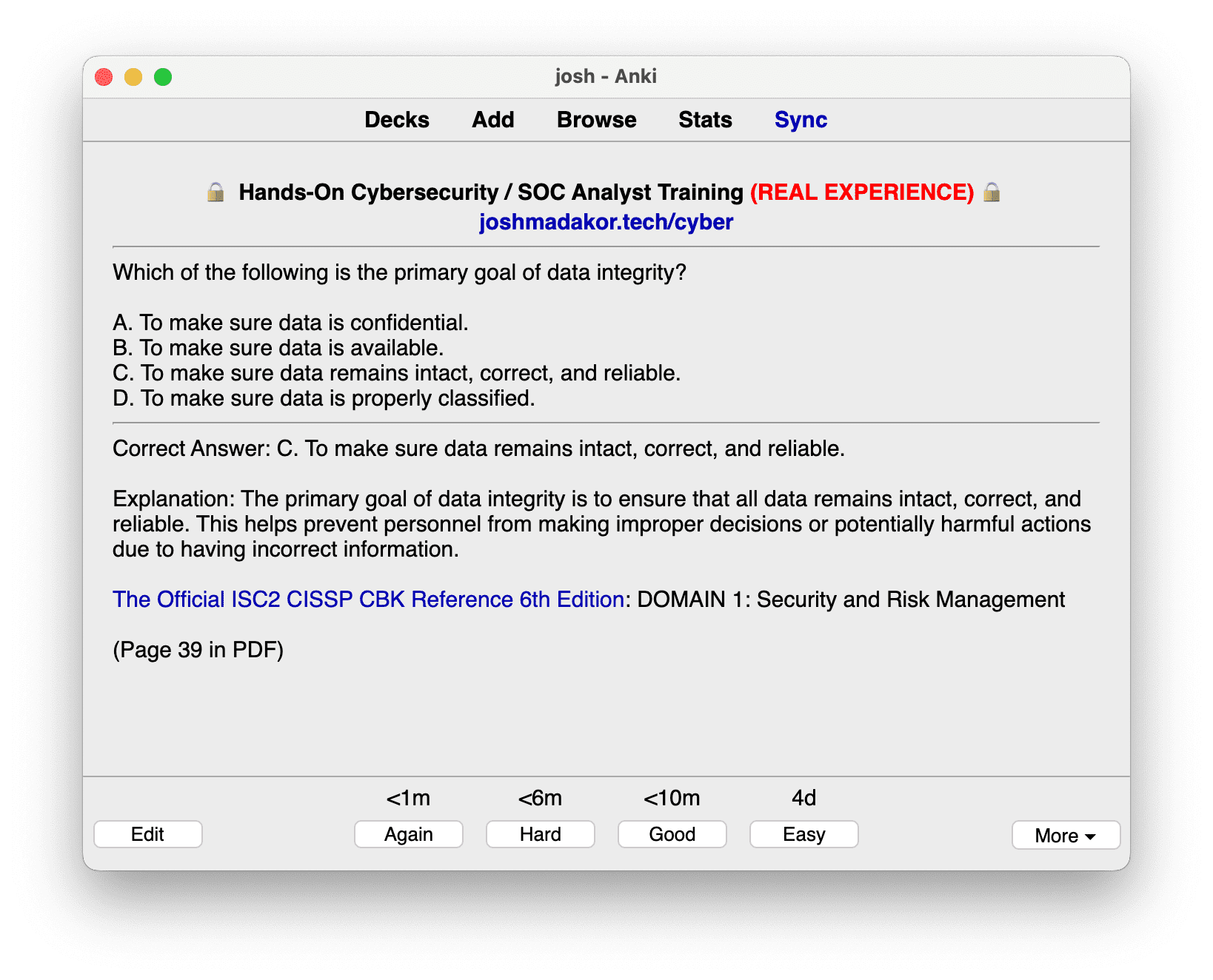
Domain 1 CISSP Exam: Security and Risk Management Begin your CISSP certification journey with a deep dive into Domain 1: Security and Risk Management, a cornerstone of the CISSP exam. This domain covers a wide range of crucial topics, including:
- Risk Management: Gain comprehensive insights into risk identification, evaluation, and prioritization. Learn how to develop and implement risk management strategies that are aligned with organizational objectives and ensure a robust defense mechanism against potential threats.
- Asset Security: Explore the nuances of protecting and managing assets. Understand the importance of data classification, ownership, and protective measures to maintain the integrity, confidentiality, and availability of information assets.
Our comprehensive Domain 1 CISSP Exam for Domain 1 is meticulously crafted by cybersecurity experts. It offers a realistic CISSP exam experience with detailed answer explanations for each question, enhancing your knowledge and understanding of complex security topics.
With this all-encompassing practice test, prepare to excel in CISSP Domain 1: Security and Risk Management. Empower your cybersecurity career with a strong foundation in the principles of security governance, risk management, and compliance.
Back to All CISSP Domains / Home
Explore our other free practice tests:
- CISSP Practice
- CompTIA A+ Practice
- CompTIA Network+ Practice
- CompTIA CySA+ Practice
- CompTIA Security+ Practice
- ITIL Practice