🔒 Hands-On Cybersecurity Course + INTERNSHIP 🔒
CISSP Domain 3: Mastering Security Architecture and Engineering
Ready to conquer CISSP Domain 3? This crucial domain focuses on the foundations of secure system design and implementation.
Key Topics in Domain 3:
- Security Models and Frameworks
- Cryptography Principles and Applications
- Secure System Design Principles
- Security Capabilities of Information Systems
- Security Assessment and Testing
- Physical Security Measures
These topics are essential for both the CISSP exam and real-world cybersecurity practices. You’ll learn to design, implement, and maintain secure systems using industry-standard models and cutting-edge techniques.
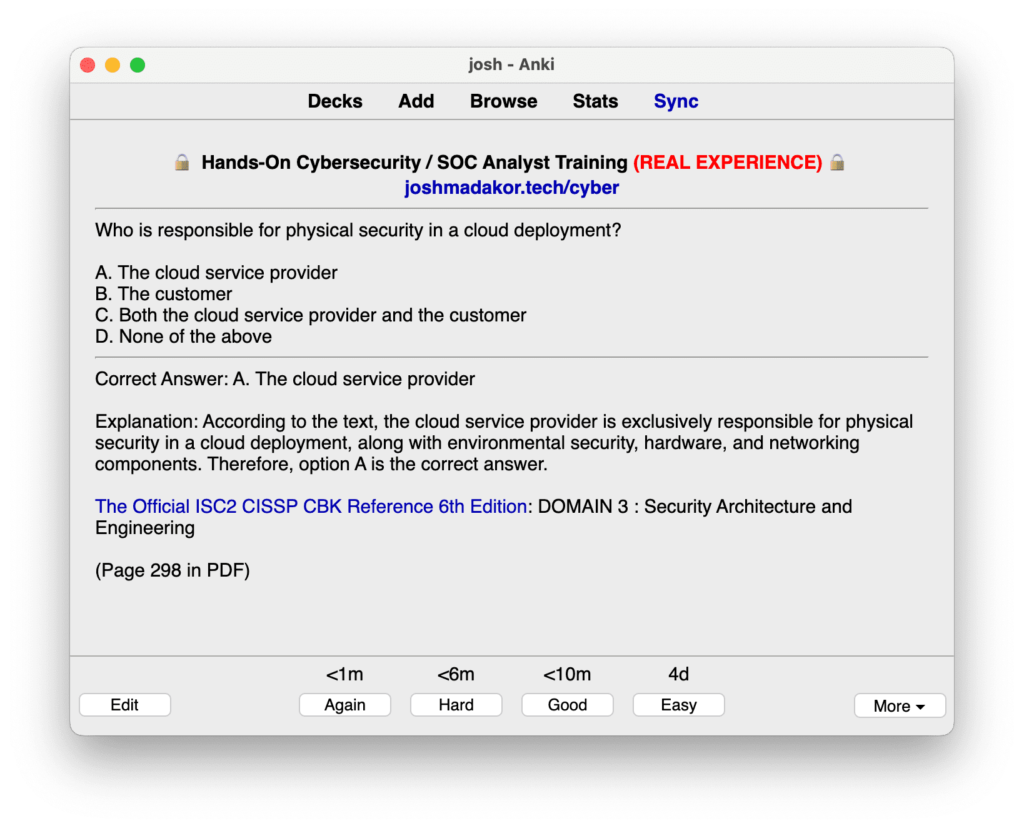
Practice Exam
Our free CISSP practice exam is based on the official question book (The Official ISC2 CISSP CBK Reference 6th Edition).
Each question is accompanied by a detailed explanation to help you better understand complex security concepts.
Continuous Learning
To broaden your knowledge, revisit Domain 2: Asset Security and explore Domain 4: Communication and Network Security.
For official exam information, visit the ISC² CISSP page.
Start your journey to CISSP success today! Use this guide and our practice tests to confidently approach Domain 3 and advance your cybersecurity career.