🔒 Hands-On Cybersecurity Course + INTERNSHIP 🔒
Understanding the Core of Domain 5
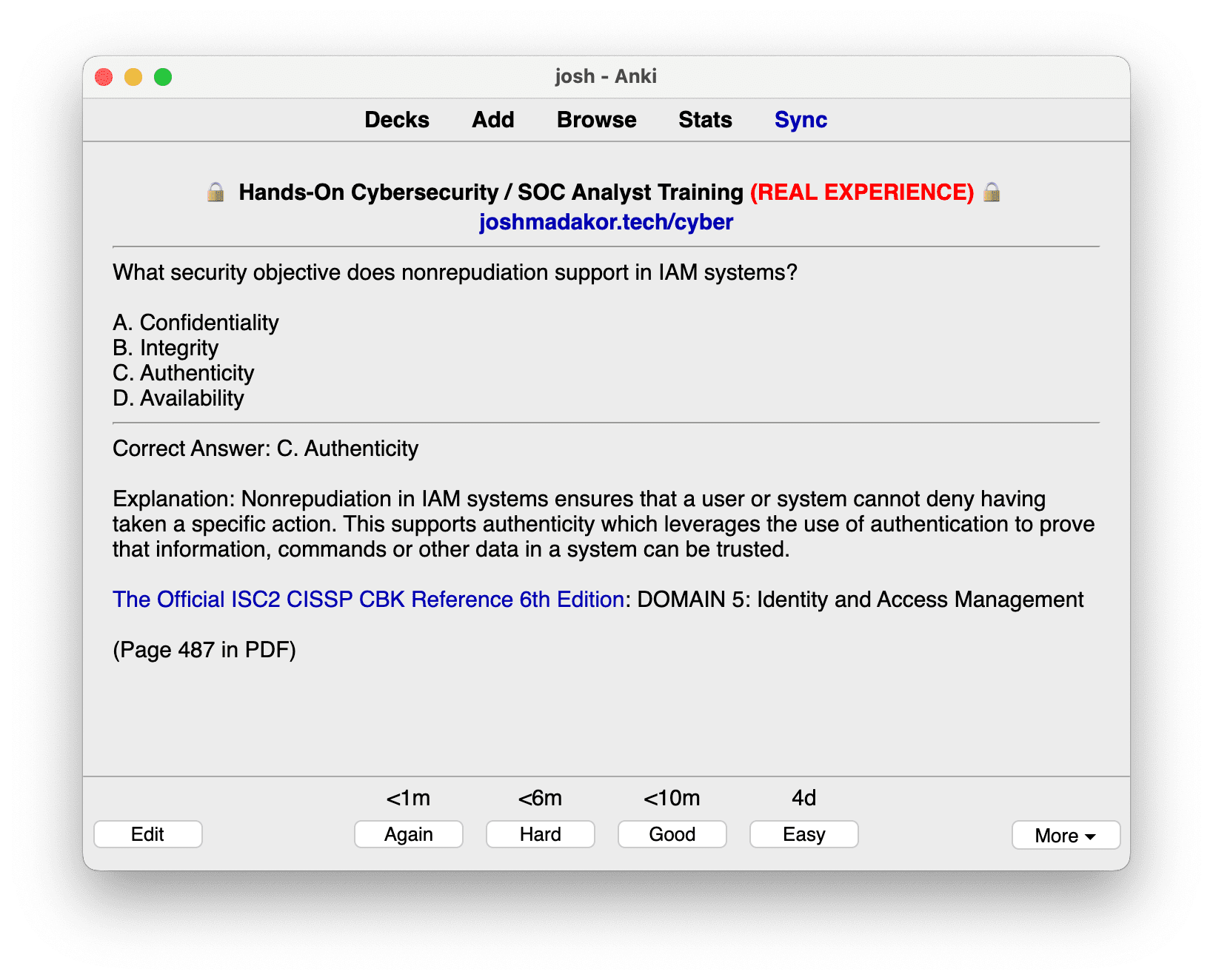
Domain 5: Identity and Access Management is a critical component of the CISSP Practice Exam, focusing on managing and securing identity and access within an organization. This domain ensures that the right individuals have the appropriate access to technology resources.
Key Areas in Domain 5 (Identity and Access Management) within the CISSP Exam
The Domain 5 of CISSP covers various areas, including:
- Identity Management: Mechanisms for user registration and creation of digital identities, essential for establishing trust.
- Access Management Systems and Methodologies: Ensuring only authorized individuals access specific data or systems.
- Identity as a Service (IDaaS): Cloud-based identity services, crucial as organizations move to cloud computing.
Enhancing Your Skills with Our CISSP Practice Exam
Take our free CISSP Practice Test for Domain 5 above. This test prepares you for the CISSP Exam and deepens your understanding of Identity and Access Management with high-quality questions and detailed explanations.
Conclusion
Domain 5 of the CISSP Exam is crucial for understanding Identity and Access Management. Our practice exam enhances your knowledge and skills, essential for effective security management in any organization.