🔒 Hands-On Cybersecurity Course + INTERNSHIP 🔒
CISSP Domain 8: Mastering Software Development Security
Are you ready to tackle CISSP Domain 8?
This domain emphasizes the importance of secure software development practices in information security.
Key topics covered in Domain 8:
-
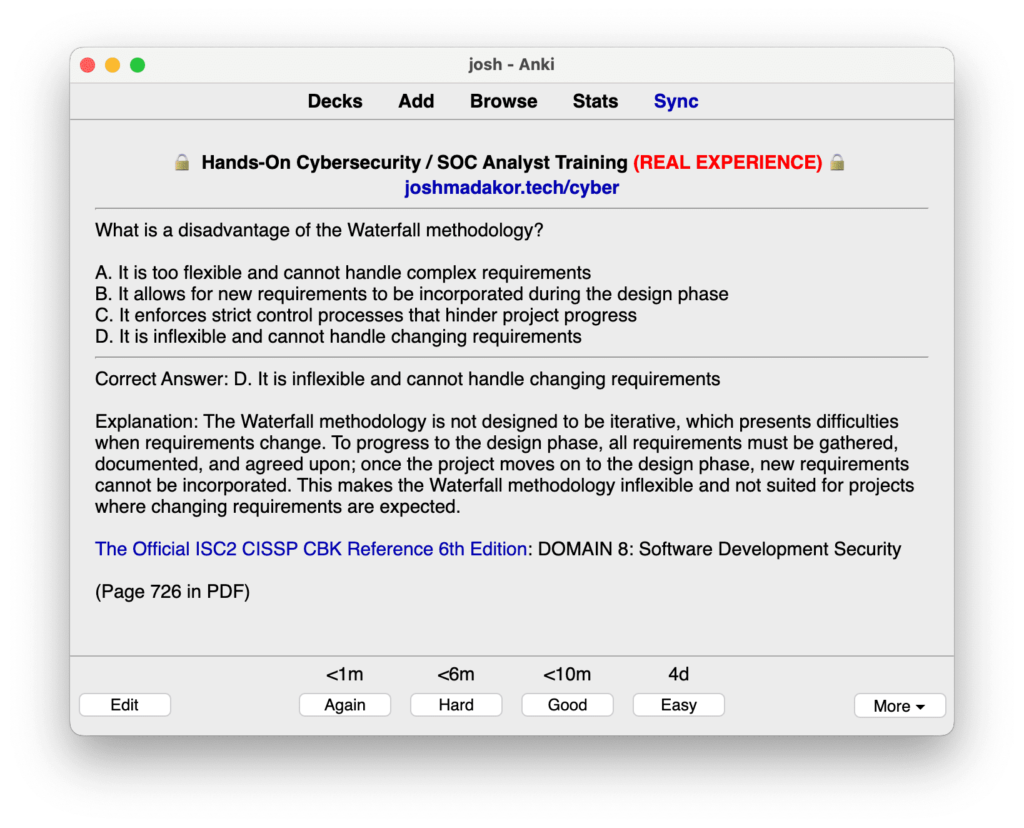
- 1.Secure Software Development Life Cycle (SDLC)
-
- 2.Secure Coding Practices
-
- 3.Application Security Controls
-
- 4.Software Vulnerability Testing
Mastering Domain 8 for CISSP Success
This knowledge is crucial not only for passing the CISSP exam but also for your career in cybersecurity. You’ll learn how to integrate security throughout the development process, avoid common vulnerabilities, and implement effective security measures.
Utilize Free CISSP Practice Tests
Utilize our free CISSP practice tests to assess your knowledge. These tests, complete with detailed explanations, will help you prepare thoroughly for the exam.
Beyond the Exam: Developing Essential Skills
Mastering Domain 8 goes beyond passing the exam. It’s an opportunity to develop skills in creating secure and reliable software, positioning you as a true information security professional. For official information, visit the ISC² CISSP page.
We wish you success on your CISSP journey.
Use this guide and the practice tests to approach Domain 8 with confidence!