Dowload the FREE OFFLINE Version of this Test Bank
Boost your cybersecurity skills! Click to download the CompTIA CySA+ Anki deck.
Enhance Your Cyber Security Skills with Our Free CompTIA CySA+ (CS0-003) Domain 1: Security Operations Practice Test!
Are you preparing for a career transition into IT or aiming to enhance your IT skills? Our free CompTIA CySA+ (CS0-003) Domain 1: Security Operations practice test is here to help you succeed. This test mirrors the actual exam format, boosting your confidence and readiness.
Key Features
Realistic Exam Simulation:
Experience the actual CompTIA CySA+ exam format, helping you get accustomed to the test environment.
Comprehensive Explanations:
Each question comes with detailed explanations, allowing you to learn from your mistakes and deepen your understanding.
Identify Weak Areas:
Pinpoint your weaknesses and focus your study efforts where they are needed most.
Completely Free:
Access our high-quality practice test at no cost and start preparing for your CompTIA CySA+ certification today.
Why Choose Our Practice Test?
Expertly Crafted:
Created by industry professionals with extensive experience in cybersecurity.
Career Advancement:
Passing the CompTIA CySA+ certification can open doors to new job opportunities in the IT field.
Convenient and Accessible:
No registration required. Take the test online anytime, anywhere.
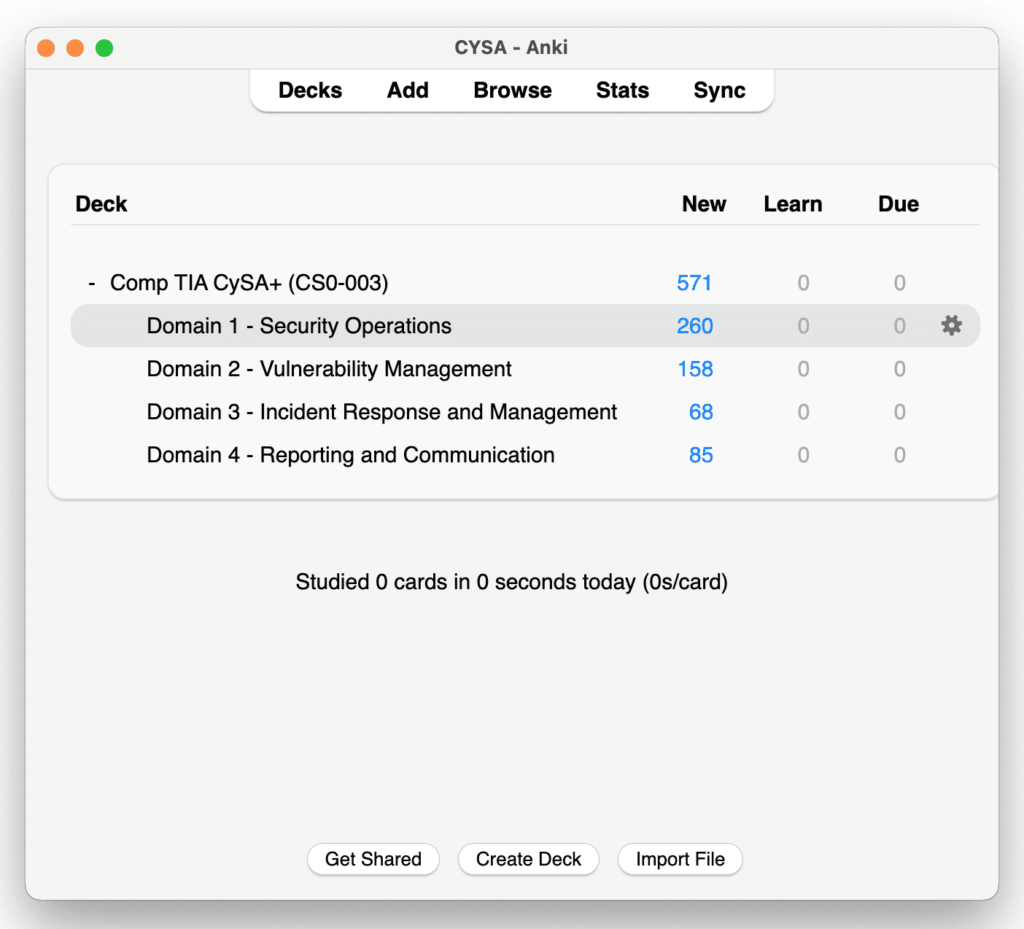
Free Anki Deck Download
Download our free Anki Deck, reviewed by industry expert Josh Madakor, who has extensive experience in IT and cybersecurity, including work with Microsoft and government sectors. Learn more about Anki on the official site.
Prepare yourself for the CompTIA CySA+ (CS0-003) certification exam by mastering Security Operations. Ideal for those looking to enhance their cybersecurity skills, achieve certification, and advance their careers in IT. For more information, visit the CompTIA CySA+ official site.
Don’t wait—start mastering Domain 1: Security Operations for the CompTIA CySA+ (CS0-003) exam today with our free practice test!