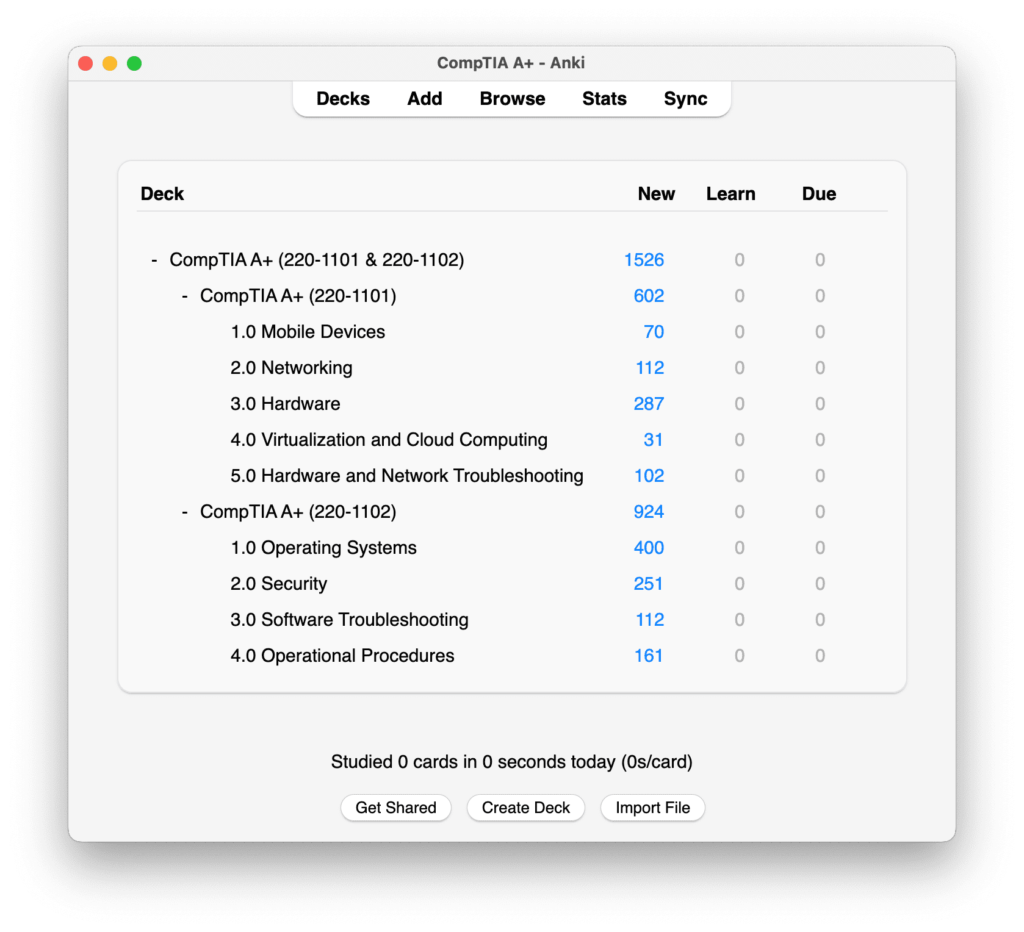
Dowload the FREE OFFLINE Version of this Test Bank
Get ready to improve your skills offline now! Click the download button.
Free CompTIA A+ 220-1102 Security Practice Test
The Ultimate Free Practice Test for CompTIA A+ Exam Preparation
Are you aiming to transition into the IT industry or enhance your cybersecurity skills? Our free CompTIA A+ 220-1102 Security practice test is designed to help you succeed. This practice test supports your CompTIA A+ exam preparation, skill enhancement, and career advancement in the IT industry.
Features of Our Practice Test
- Realistic CompTIA Exam Simulation: Familiarize yourself with the format and types of questions on the actual exam.
- Skill Enhancement: Strengthen your knowledge in critical areas such as vulnerability management, security, and cybersecurity.
- Career Change Support: Ideal for those considering a career change or seeking to enter the IT field.
- Cybersecurity Understanding: Deepen your understanding of essential cybersecurity principles.
Why Choose Our Practice Test?
Our free CompTIA A+ 220-1102 Security practice test is perfect for individuals aiming to enhance their skills and effectively prepare for the CompTIA A+ exam. Whether you’re looking for a job change or wanting to gain more experience in the IT industry, our practice test is your ideal solution.
Start Your Practice Test Today
Begin your journey to CompTIA A+ certification and unlock new opportunities in the IT industry. Access our free practice test and start your preparation now! Improve your IT skills, gain valuable experience, and pave the way for a successful career in cybersecurity and vulnerability management.