Dowload the FREE OFFLINE Version of this Test Bank
Boost your cybersecurity skills! Click to download the CompTIA Security+ Practice Anki deck.
Free CompTIA Security+ Practice Test – Chapter 01: Mastering Security Basics
Mastering Security Basics for CompTIA Security+ is essential for anyone pursuing the certification. This chapter offers free practice questions to help you strengthen your foundational security knowledge. Boost your IT skills with our free CompTIA Security+ practice test focusing on Chapter 01: Mastering Security Basics. Whether you’re entering the IT industry or advancing in cyber security, our resources are here to help you succeed in the CompTIA Exam.
Why Choose Our CompTIA Security+ Practice Test?
- Skill Enhancement: Covers essential security basics and concepts crucial for the CompTIA Exam and vulnerability management.
- Career Advancement: Passing the CompTIA Security+ exam can open doors to new job opportunities and significant career changes in the IT industry.
- Vulnerability Management: Master the art of managing security vulnerabilities, a key skill in the field of cyber security.
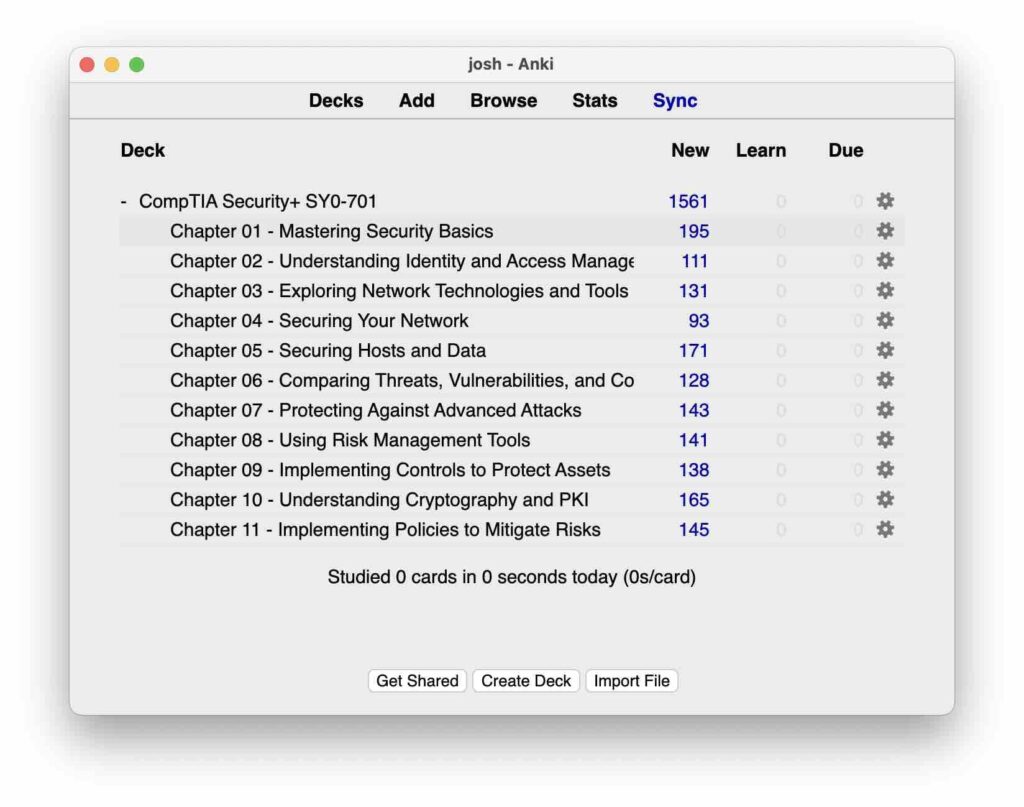
Free Anki Deck Download
Download our free Anki Deck, reviewed by industry expert Josh Madakor, who has extensive experience in IT and cyber security, including work with Microsoft and government sectors. Learn more about Anki on the official site.
Get Started with Your IT Career Change Today!
Visit the CompTIA Security+ official site and the CompTIA Network+ official site for more information.